Beyond Bitcoin: AI, Stablecoins, and the Future of Money
Part 4, The Identity Revolution
The Question That Changed Everything:
The banking app on our undergrad’s computer (remember her from Part 3?), is asking her a question that seems simple enough, “Is this you?” In that scenario, several anomalies in her normal behavior were detected by AI, which then prevented attackers from stealing her money from her stablecoin wallet. This happened within seconds. Without this technology, her money would have been gone.
This is about identity. Not the identity she proved once when she opened an account, but the identity that must be proven continuously, every transaction, every interaction, in a financial system that moves too fast for second chances.
Identity Revolution Part 1: The Old Way Is Broken
The Point-in-Time Trap: For decades, financial identity worked like getting a passport. You prove who you are once and receive a credential that’s valid for ten years. Banks did the same thing: verify identity at account opening, then trust that verification forever.
This made sense in a world where:
Transactions took days to settle (time to catch mistakes)
Chargebacks existed (reverse fraudulent transactions)
Geographic friction provided security (hard to rob a bank in New York from Nigeria)
Human reviewers spot-checked suspicious activity (during business hours)
But that world is evolving. Stablecoins move money in seconds. Settlement is instant and irreversible. Geography is meaningless. Attacks can happen at any hour any day. The old identity model, verify once, trust forever, collapses when there’s no time to fix mistakes and no way to reverse transactions.
Traditional identity verification checklist:
Correct username and password
Correct answers to security questions
Voice authentication passed (AI-generated clone sounds exactly like our undergrad)
Transaction initiated from registered device (malware gave attacker access)
Within bank’s transaction limits
With every box checked, the system will say “verified” and money will be moved. By the time the old way discovers the mistake the money has been split across 47 different wallets, moved through three mixing services, and converted into different cryptocurrencies.
The old system was designed for a world where banks could reverse wire transfers, transactions took days to clear, and humans reviewed suspicious activity during business hours. That world doesn’t exist anymore. Stablecoins move money in seconds, and those seconds happen at 3 AM on Sunday just as easily as 2 PM on Tuesday.Traditional identity, verifying “who you were” when you opened the account, cannot protect you in a system where money moves at digital speed and attackers use AI to impersonate you perfectly. This is why identity infrastructures have to be rebuilt from the ground up with multiple dimensions.
Identity Revolution Part 2: The Three Authentication Dimensions of Modern Identity Infrastructures (Seeing What Humans Can’t)
To address the stablecoin’s fraud paradigm, identity infrastructures have evolved to include three interconnected dimensions that work together to answer “Is this really you?”
Dimension 1: Who You Claim to Be (Identity Assertion) This is the traditional dimension: credentials like passwords, biometrics, device fingerprints, and possession factors (SMS codes, authenticator apps). It answers: “Do you have the right keys?” But these can be stolen, so they’re just the starting point.
Dimension 2: How You Behave (Behavioral Biometrics) This dimension measures the invisible patterns unique to you: typing speed and rhythm, mouse movements, navigation patterns, how you interact with technology across hundreds of subtle dimensions built over thousands of sessions. It answers: “Do you act like the real person?” This is nearly impossible to fake perfectly.
While attackers may know the victim’s username and password, the system is measuring something the attacker doesn’t even know exists: behavioral biometrics. Even if you’ve stolen someone’s password and device, you can’t steal the unique way they interact with technology embedded in muscle memory and habit patterns. These behavioral biometrics are nearly impossible to fake across all dimensions simultaneously.
Dimension 3: What’s Happening Around You (Context Intelligence) This dimension analyzes everything surrounding the transaction: time of day, location, device characteristics, recent account activity, transaction patterns, network intelligence, external threat data, and correlation with known attack patterns. It answers: “Does this situation make sense?” Individual signals might be innocent, but patterns reveal the truth. Behavioral patterns can vary. Our undergrad might be tired, rushed, or stressed. Behavioral biometrics alone shouldn’t block a transaction, but combined with everything else, they paint a picture.
The system knows things the attacker doesn’t realize it knows. For instance:
Recent Activity Timeline:
2 days ago: Password change requested from IP address in Eastern Europe (failed after SMS verification)
1 day ago: Multiple failed login attempts from same IP
12 hours ago: Undergrad’s email account logged unusual activity alert (someone tried accessing from East European city)
3 hours ago: Undergrad’s phone number appeared in dark web monitoring (recent data breach)
Transaction Context:
Time: 2 AM (undergrad’s historical logins: 99% between 8 AM and 6 PM)
Amount: $12,000 (average transaction: $500, maximum previous: $800)
Recipient: New wallet address (never sent money here before)
Transaction type: International wire to cryptocurrency exchange (never done this before)
Device Context:
IP address: VPN service (Undergrad normally connects from home network)
Location claim: Chicago (Undergrad’s normal location)
Actual location indicators: VPN endpoint in Netherlands (spoofing location)
Time zone: Browser time zone set to Amsterdam (doesn’t match claimed Chicago location)
Network Context:
This IP address attempted logins at 47 other banks this week (credential stuffing attack pattern)
15 of those attempts were successful (same password reuse pattern)
Those successful logins all resulted in fraudulent transfers within 24 hours
This IP is flagged in shared fraud database as a known bad actor
External Context:
Undergrad’s email: Received phishing attempt 3 days ago claiming to be from bank
Recipient wallet: Appears in 12 suspicious activity reports (SAR) from other banks this month
Transfer amount: $12,000, account total but well below bank’s threshold requiring extra review
Modern system reasoning:
Password valid: (but was stolen)
Behavioral biometrics: 61-73% match (wrong person)
Recent activity: 4 red flags (password change attempts, failed logins, fraud research)
Transaction context: 4 red flags (time, amount, recipient, type, location)
Device context: 4 red flags 73% match (unrecognized device)
Network context: 4 red flags (VPN, known bad IP, time zone mismatch, attack patterns)
External context: 3 red flags (phishing, known bad recipient, transfer amount)
Total assessment: 19 red flags. Probability this is legitimate: 4%. Probability this is fraud: 96%.
The Decision Point (2:00:05 AM):
Modern Identity System: “FRAUD DETECTED - Transaction blocked immediately”
Automated response (happens in 5 seconds):
Block the transaction before processing
Freeze the account temporarily
Send urgent alerts to all Undergrad’s registered devices:
SMS: “SECURITY ALERT: Suspicious login blocked. If this was you, call immediately.”
Email: Same alert
Push notification: Same alert
Automated phone call: “This is your bank. We blocked a suspicious $12,000 transaction. Press 1 if this was you, press 2 if this is fraud.”
Undergrad’s Response: Presses 2. Half-asleep, but immediately understands someone tried to rob her.
System Response:
Initiates password reset (old password now invalid)
Requires in-person identity verification before account reactivation
Files fraud report with law enforcement
Adds attacker’s IP and patterns to global fraud database
Notifies other institutions about this attack pattern
6 AM - Undergrad Checks Her Account: Balance: $12,000. Still there.
Together these dimensions create continuous verification: Not “were you verified three years ago” but “are you really you right this second,” answered across 100+ signals in real-time, every transaction, with 95%+ accuracy. The key insight: No single dimension is sufficient. Credentials can be stolen. Behavior can be mimicked. Context can be spoofed. But faking all three simultaneously? Nearly impossible.
Traditional System: “All credentials valid. Transaction approved.” $12,000 sent. Undergrad’s future jeopardized.
Identity Revolution Part 3: The Agent Identity Problem (When Money Moves Without Humans)
What happens when the “person” initiating transactions isn’t a person at all, but an AI agent?
The Treasury Agent Scenario
Acme Corporation has operations in 12 countries. Their treasury team used to have eight people manually managing accounts, moving money, optimizing cash positions. Now they have a treasury agent, and an agentic AI system that does all of this autonomously, 24/7.
Monday, 6:47 AM - The Agent Awakens
The system perceives: Singapore account will fall below minimum balance by end of day. Forecasts: $500,000 shortfall. Required action: Transfer funds from US account.
The agent decides: Move $500,000 USDC from US account to Singapore account. Optimal rail: Stablecoin (arrives in minutes, costs $12 vs. $450 wire fee).
The agent acts: Initiates transfer. $500,000 begins moving.
The identity question: How does the bank know this is Acme’s legitimate treasury agent and not a hacker who compromised the agent’s credentials? This is the unsolved problem that’s now becoming urgent: agent identity.
What Makes Agent Identity Different (And More Difficult)
Human Identity Verification:
Biometrics: Face, fingerprint, voice (unique to each person)
Behavior: How you type, move mouse, navigate (built over years)
Context: Where you are, what time you work, your patterns
Recovery: If credentials stolen, human can prove identity in person
Agent Identity Verification:
Biometrics: None (agents don’t have faces or fingerprints)
Behavior: Algorithmic (consistent, not human-variable)
Context: Operates 24/7 from servers (no normal hours or location)
Recovery: If compromised, no real agent can show up to prove identity
The attack vector is different too:
Attacking a Human: Steal password + Fake biometrics + Mimic behavior + Hope human doesn’t notice
Attacking an Agent:
Compromise the server hosting the agent
Inject malicious code into agent’s decision logic
Intercept API calls and modify instructions
Impersonate agent to systems it interacts with
Change agent’s goals without anyone noticing for days
Example Attack - The Modified Treasury Agent:
Someone hacks Acme’s servers and modifies the treasury agent’s code. The change is subtle:
ORIGINAL CODE:
If (need to move funds):
Transfer to: Acme’s Singapore account
MODIFIED CODE:
If (need to move funds AND amount > 4100,000):
Transfer to: Attacker’s anonymous wallet
ELSE
Transfer to: Acme’s Singapore account
Small transfers work normally. Large transfers get stolen. It might take weeks before anyone notices, and by then, millions could be gone. How is this prevented?
The Agent Identity Framework (Solving the Problem)
Modern agent identity uses a multi-layered approach that treats agents like skilled employees who need both credentials and continuous performance monitoring.
Dimension 1: Agent Certificates (Who Is This Agent)
Just like websites have SSL certificates proving “this is really chase.com and not a phishing site,” agents need identity certificates such as:
AGENT IDENTITY CERTIFICATE:
Agent ID: treasury-agent-acme-corp-prod-001
Issued To: Acme Corporation
Issued By: First National Bank (Trusted Authority)
Valid: 2026-01-01 to 2027-01-01
AUTHORIZED CAPABILITIES:
View all account balances
Initiate transfers up to $1M per transaction
Execute FX trades up to $500K per trade
Generate financial reports
RESTRICTIONS:
Cannot transfer to new recipients without human approval
Cannot change account structures
Cannot modify its own authorities
OPERATIONAL BOUNDARIES:
Maximum daily transfer volume: $10M
Geographic scope: US, Singapore, UK, Germany
Operating hours: 24/7
Requires human approval for: Transactions > $1M, New payees, Policy changes
AGENT CRYPTOGRAPHIC SIGNATURE:
Public Key Infrastructure (PKI) Digital Signature - Tamper-Proof
This certificate is cryptographically signed. If anyone modifies the agent’s code or tries to impersonate it, the signature won’t verify. The certificate is checked with every action.
Dimension 2: Behavioral Baselines (Is This Agent Acting Normally?)
Even with valid credentials, the system monitors whether the agent is behaving like itself:
Normal Treasury Agent Behavior (Learned Over 6 Months):
Average daily transfers: 15
Average transfer size: $250,000
Typical recipients: 8 regular internal accounts
Preferred rail: 60% stablecoin, 40% wire
Decision pattern: Moves money in morning hours (6-9 AM US time)
FX strategy: Converts when rates favorable, typically waits for 0.3% advantage
Error rate: 0.01%
Anomalous Behavior (What Would Indicate Compromise):
Transfer spike: 47 transfers in one day (213% above baseline)
Size anomaly: Avg transfer $890,000 (256% above baseline)
New recipient: Cryptocurrency exchange (never transacted before)
Rail change: 100% wire transfers (avoiding stablecoin’s transparency)
Timing shift: Transfers at 3 AM (unusual for this agent)
Strategy change: Not waiting for favorable rates (rushing)
Error spike: 3 failed transfers (execution errors suggesting modified code)
System reasoning: This agent is behaving nothing like itself. Probability of compromise: 94%.
Automated response:
Suspend agent immediately (stop all transactions mid-execution)
Alert human supervisors (CFO, CTO, security team)
Initiate forensic analysis (examine agent code for modifications)
Quarantine agent (prevent it from communicating with other systems)
Roll back to last known-good version if compromise confirmed
Human investigation findings: Agent code was modified three days ago during routine maintenance. The modification wasn’t authorized. Security breach confirmed.
Outcome: $4.7M in fraudulent transfers were attempted and all were blocked. Zero loss.
Without behavioral monitoring: The modified agent would have appeared legitimate (correct credentials, valid certificate), and stolen millions before anyone noticed.
Dimension 3: Multi-Party Authorization (Checks and Balances)
For high-risk actions, even legitimate agents need approval from multiple parties:
Scenario: Agent Wants to Transfer $5M to New International Account
Single-Party Risk: If agent is compromised, attacker controls everything
Multi-Party Solution:
TRANSACTION APPROVAL WORKFLOW
Initiated By: Treasury Agent (6:47 AM)
Amount: $5,000,000 USDC
From: US Operating Account
To: New account in Cayman Islands
Reason: “Establishing offshore treasury management”
REQUIRED APPROVALS:
Treasury Agent: Initiated and recommends
CFO: Approved via mobile app (6:52 AM)
Compliance Agent: BLOCKED - Sanctions review required
[Pending] Bank Risk System: Awaiting compliance clearance
STATUS: Transaction held pending compliance review
TIMEOUT: If not approved within 4 hours, transaction auto-cancels
The CFO approved (legitimate business need), but the compliance agent (a separate AI system responsible for regulatory checks), flagged it. A new account in Cayman Islands requires enhanced due diligence, which initiates a reasonable delay for verification.
If the treasury agent had been compromised: Even with CFO approval, the compliance agent would catch suspicious patterns (why Cayman Islands? Why new account? Why $5M all at once?). Multi-party authorization means no single point of failure.
This mirrors how corporations already work: No single employee can wire $5M without approval. Separation of duties, and checks and balances are standard practices. The same principles apply to AI agents—maybe more so, because agents can be compromised in ways humans can’t be.
Identity Revolution Part 4: How Modern Identity Transforms Stablecoin Operations (The Complete Lifecycle)
Here we trace identity’s role through every stage of a stablecoin’s existence, showing how it’s fundamentally different from traditional approaches.
Stage 1: Issuance (Birth of a Token)
Traditional Identity (2015 Model):
Customer applies for account
Submit documents (passport scan, utility bill)
Human reviewer verifies (takes 1-3 days)
Account approved, customer can now mint stablecoins
Identity verification complete (never checked again)
Problems: That verification is three years old. The real person might not even have access to the account anymore (credentials stolen, device compromised, account taken over). But the system still trusts that years-old verification.
Modern Identity (2025 Model):
9 AM – Our Undergrad Wants to Mint (Issuance) 10,000 USDC
She sends $10,000 wire transfer to Circle. Traditional system would verify the wire, check that her account was KYC-approved years ago, and mint tokens. Modern system does something different. It performs identity verification in real time, which takes about 90 seconds.
Step 1: Document Intelligence
Her account: Verified 2 years ago with passport
Check: Is that passport still valid? (Yes)
Cross-reference: Has passport been reported stolen? (Check with State Department API)
Verify: Does recent activity match person who opened account? (Behavioral analysis)
Step 2: Source of Funds Analysis
Wire came from: Bank of America, account holder our undergrad
Check: Is this the same bank account used previously? (Yes)
Verify: Has this bank account been flagged for fraud? (No)
Pattern analysis: Amount $10,000 fits her typical deposit range ($5K-$15K)
Step 3: Behavioral Verification
Device: Same cell phone she always uses
Location: Chicago (our undergrad’s normal location)
Timing: 9 AM weekday (typical for her)
Navigation: Checked balance first, then initiated mint (her pattern)
Step 4: Contextual Intelligence
Recent activity: No password changes, no failed logins, no fraud reports
External signals: No dark web mentions of the undergrad’s credentials
Network analysis: Her IP address has clean history
Social signals: No concerning posts about “hacked” or “lost access”
Risk Assessment: 8/100 (Very Low)
9:01:30 AM - Decision: Auto-approve and mint 10,000 USDC
Total time: 90 seconds. But unlike the traditional instant approval based on years-old verification, this approval is based on right-now confidence that:
The person who opened the account three years ago is the same person requesting tokens today
No indicators of account takeover or compromise
Behavioral patterns match expected norms
External intelligence confirms no known threats
This is identity that expires every 90 seconds and must be continuously re-earned.
Scenario: What if This Wasn’t Our Undergrad?
Same situation, but our undergrad’s credentials were stolen yesterday. Attacker tries to mint tokens.
9 AM - Attacker’s Attempt
Real-Time Verification Detects:
Device: New Android phone (never seen before)
Location: VPN endpoint (not her normal network)
Timing: 3 AM (the undergrad never banks this early)
Navigation: Went straight to “Mint” without checking anything (not her pattern)
Behavioral: Typing speed and mouse movements don’t match her behavioral characteristics
Contextual: Password was changed 18 hours ago from suspicious IP
Risk Assessment: 91/100 (Critical)
9:00:05 AM - Decision: BLOCK and require enhanced verification
Automated Actions:
Transaction blocked before processing
Account temporarily frozen
SMS/email/push alerts to all of our undergrad’s devices: “Suspicious activity detected. Was this you?”
Required verification: Video call with support (prove it’s really her by showing face + ID)
If she confirms fraud: Initiate investigation, file reports, reset credentials
Outcome: Attacker blocked in 5 seconds. Her $10,000 never minted for attacker. Zero loss.
Stage 2: Circulation (Monitoring Every Transaction)
Once tokens are minted and circulating, identity verification doesn’t stop. Every transaction is an opportunity to verify that the holder is still legitimate.
Continuous Transaction Monitoring:
The undergrad’s 10,000 USDC moves through the ecosystem. The identity system watches every hop:
Transaction 1: Undergrad → Online Retailer (300 USDC for purchase)
Merchant: Known, legitimate, good reputation
Amount: Normal for this merchant category
Her pattern: Has shopped online before
Risk: 12/100 (low) → Process normally
Transaction 2: Undergrad → Her Own New Wallet (5,000 USDC for portfolio organization)
Recipient: New address (potential flag)
But: Same device, same behavioral patterns, address created from same wallet app
Purpose inference: Likely portfolio reorganization (common pattern)
Risk: 18/100 (low) → Process, but monitor new address for unusual activity
Transaction 3: Undergrad → Friend (500 USDC repaying loan)
Recipient: New address (flag)
But: her email shows recent discussion “I’ll send you that $500 on Friday”
Device/behavior: Consistent with the undergrad’s
Amount: Matches email discussion
Risk: 15/100 (low) → Process normally
Transaction 4: Undergrad Receives 200 USDC from Unknown Address
Sender: Address flagged in ransomware investigation (major flag)
But: Tracing shows Ransomware victim → Recovery service → Mixer → Exchange → Undergrad
She’s likely unaware of source (5 hops removed)
Risk to the undergrad: Low (she’s victim of contaminated funds, not criminal)
Action: No block (she’s innocent), but flag for monitoring (if she sends to high-risk address next, more scrutiny)
What the Identity Infrastructure Does:
Builds comprehensive profile of “normal” vs. “suspicious”
Doesn’t just look at individual transactions
Analyzes patterns, relationships, context, timing
Distinguishes between “user organizing their finances” and “criminal laundering money”
Example of Suspicious Pattern Detection - Different user, different pattern:
User X Receives 50,000 USDC:
Source: Tornado Cash mixer (major flag - used for money laundering)
Immediately splits into 50 transactions of 1,000 USDC each (classic layering)
Sends to 50 different new wallets (spraying to obscure trail)
Those wallets send to darknet market addresses (illegal goods)
Identity System Assessment:
This is textbook money laundering
Pattern seen in thousands of criminal cases
User X is either criminal or willing money mule
Automated Response:
Flag all 50 related addresses
Hold any attempted off-ramp (conversion back to fiat)
File Suspicious Activity Report (SAR) with Financial Crimes Enforcement Network (FinCEN)
Share anonymized pattern with other institutions
If user attempts to redeem: Freeze funds, require explanation, potential law enforcement referral
The multi-dimensional architecture doesn’t just verify humans. It verifies the integrity of the entire transaction network, catching criminal activity that individual transaction checks would miss.
Stage 3: Stablecoin-Specific Identity Challenges
Different stablecoin types create different identity verification needs. Identity supports each of the four types of stablecoin:
A. Fiat-Backed Stablecoins (USDC, EUROC) - Simplest, but Still Complex
Identity Challenge: Prevent fraud during on/off ramps (fiat ↔ stablecoin conversion)
Critical Moments:
Minting: Is the person requesting tokens the legitimate account holder?
Redemption: Is the person redeeming tokens entitled to do so?
Why Identity Matters Here:
Attack Vector - Redemption Fraud:
Attacker steals the undergrad’s USDC wallet credentials
Immediately redeems 10,000 USDC for fiat
Requests wire to attacker’s own bank account
Once fiat wires, it’s gone
Identity Defense:
Verify: Is this redemption request coming from the undergrad’s normal patterns?
Check: Redemption bank account. Is this the same one used for original deposit?
Analyze: Behavioral biometrics. Does this look like her typical interaction?
Correlate: Any recent password changes, failed logins, or compromise indicators?
If all checks pass: Process redemption normally (2 minutes). If flags appear: Require enhanced verification (video call, additional documentation).
The identity layer makes fiat-backed stablecoins as secure as traditional banking while maintaining speed advantage.
B. Crypto-Backed Stablecoins (DAI, others) - Complexity Squared
Identity Challenge: Verify not just humans but also smart contracts and collateral positions
The Scenario:
$150,000 of Ethereum is deposited as collateral
Mints $100,000 DAI stablecoin against it
If ETH price crashes and depositor’s collateral ratio drops too low, position gets liquidated
The depositor loses everything
Critical Verification Points:
1. Position Opening (Depositing Collateral):
Standard identity verification (is this the correct individual depositor?)
Additional check: Is this amount consistent with the depositor’s typical DeFi activity?
Wallet analysis: Is this wallet’s history consistent with sophisticated DeFi user?
Risk assessment: Is the depositor sophisticated enough to understand liquidation risk?
2. Position Management (Ongoing):
Is the depositor actively monitoring his collateral ratio?
Behavioral pattern: Does s/he typically add collateral before liquidation risk?
Communication: Has s/he set up alerts for liquidation warnings?
Response time: When alerted, how quickly does s/he respond?
3. Emergency Actions (3 AM Crisis):
ETH crashes 30%, the depositor’s position is approaching liquidation
System sends emergency alert: “Add collateral within 2 hours or face liquidation”
3:17 AM: Someone logs in from the depositor’s device and adds collateral
Identity question: Is this the depositor (awakened by alert) or an attacker (stole credentials and is manipulating position)?
Identity Verification at 3 AM:
Device: Depositor’s registered laptop
Location: Depositor’s apartment (GPS match)
Biometrics: If laptop has fingerprint/face recognition, verified
Behavioral: Typing pattern matches depositor’s style (groggy/rushed but recognizable)
Context: Alert was sent 15 minutes ago, response time matches Depositor’s typical alert-to-action window
Transaction: Adding more collateral (defensive action, not offensive theft)
Decision: Allow transaction. Risk that this is attacker: 8%. Risk of not allowing transaction and depositor losing $150K to liquidation: 92%. The identity system must be smart enough to recognize: “This looks weird (3 AM, rushed typing) but is probably legitimate (device, location, defensive action) so allow but monitor closely.”
But what if behavioral patterns didn’t match?
Alternative Scenario - Attacker at 3 AM:
Device: Depositor’s laptop (stolen or remotely accessed via malware)
Location: VPN (hiding real location)
Biometrics: If available, failed or skipped
Behavioral: Typing pattern 64% match (wrong person)
Context: This is the third night in a row someone has logged in at 3 AM (normally sleeps)
Transaction type: Not adding collateral but withdrawing collateral (dangerous action)
Decision: Block transaction, freeze position, emergency call to the depositor’s phone.
This matters because in crypto-backed systems, identity verification must happen at machine speed (liquidations occur in minutes), while still being accurate enough to distinguish “panicked legitimate user” from “attacker disguised as legitimate user.”
C. Algorithmic Stablecoins (Terra/UST - Cautionary Tale) - Identity Couldn’t Save Poor Design
What Happened: To refresh your memory, here is an excerpt about this from Part 3 of our Beyond Bitcoin series:
In May 2022, $40 billion vanished in less than a week. Terra/UST, an algorithmic stablecoin with no actual backing, collapsed in a death spiral that destroyed wealth and shook confidence in all digital assets.
Could Identity Systems Have Prevented This?
No, because the design was fundamentally broken. But identity could have warned users before they lost everything.
What Identity Systems Could Have Detected:
Weeks Before Collapse:
Wallet analysis: Large “smart money” addresses (sophisticated investors) were exiting positions
Transaction patterns: UST redemptions accelerating, mint/burn ratio shifting negative
Behavioral changes: Long-term holders becoming short-term traders (sign of lost confidence)
Social sentiment: Shift from “UST is great” to “UST concerns” in online discussions
Network intelligence: Coordinated selling pressure from known attack wallets
Identity’s Role:
Warning system: “High-risk environment detected. Consider reducing exposure to algorithmic stablecoins.”
User profiling: Identify unsophisticated users (recent adopters, first-time DeFi users) and provide extra warnings
Exit facilitation: Help users understand how to safely exit positions before collapse
This occurred because no coordinated warning system existed. Sophisticated users saw warning signs and exited early. Retail users (who most needed protection) held until worthless. The lesson learned is identity verification can’t fix broken economic design, but it can protect vulnerable users by identifying them and providing targeted warnings based on their sophistication level and risk tolerance.
Modern Approach: If algorithmic stablecoins are permitted (many jurisdictions are banning them), identity systems should:
Require users to demonstrate understanding of risks before participating
Limit exposure for unsophisticated users (like broker restrictions on complex options trading)
Provide real-time risk warnings tailored to user’s knowledge level
Facilitate emergency exits when systemic risk detected
D. Synthetic Stablecoins (Basket-Backed) - Multi-Dimensional Identity
As mentioned in Part 3 of our series, synthetic stablecoins are backed by a basket of assets (example: 40% USDC, 30% T-bills, 20% bonds, 10% gold). The identity challenge is to quickly and accurately verify not just users, but also asset custody and basket composition.
The Scenario:
SynthUSD stablecoin claims to be backed by diversified basket
Identity question: Can we verify the issuer actually holds what they claim?
Identity Verification Layers:
Layer 1: Issuer Identity
Who runs this stablecoin? (Corporate entity, DeFi protocol, anonymous team?)
What’s their track record? (Previous projects, reputation, audits?)
Are they regulated? (Licensed institution vs. anonymous protocol)
Can they be held accountable? (Legal jurisdiction, insurance, recourse mechanisms)
Layer 2: Asset Custody Verification
Where are the backing assets actually held?
Can we verify ownership in real-time? (Proof-of-reserves)
Are assets segregated? (Bankruptcy-remote if issuer fails)
Who has access? (Multi-sig controls, separation of duties)
Layer 3: Composition Monitoring
Does the basket actually contain what’s claimed?
Real-time verification: “Right now, basket contains 40.2% USDC, 29.8% T-bills...”
Deviation alerts: If composition drifts from intended target, immediate notification of discrepancy
Rebalancing audit: Who can modify basket composition? Under what rules?
Layer 4: User Risk Profiling
Sophisticated users: Full disclosure, they understand complex structures
Retail users: Simplified “health score” (Green = safe, Yellow = watch, Red = exit)
Unsophisticated users: “This is a complex product. Consider simpler alternatives.”
Traditional identity verifies “Who is this person?” but Modern identity verifies “Who is this person, what do they know, what risk can they handle, and how do we protect them from risks they don’t understand?”
Example of Synthetic Stablecoin Warning:
March 2020 - COVID Market Crash: Synthetic stablecoin’s basket: 40% corporate bonds, which are crashing.
Identity System Actions:
For sophisticated users: “Portfolio rebalancing required. Bond component devalued 15%. Backing ratio now 94%. Within operational parameters but monitor closely.”
For retail users: “Warning: Market stress detected. This stablecoin’s value may fluctuate. Consider moving to fully-backed alternative.”
For unsophisticated users: “URGENT: High-risk conditions. We recommend exiting this position. Click here for step-by-step guidance.”
The identity infrastructure delivers different messages for different user identity profiles. The sophisticated user wants detailed data. The retail user wants simple guidance. The unsophisticated user needs their hand held through protective actions.
This is identity verification expanding beyond “who you are” to “who you are, what you know, and how we should communicate with you based on your capabilities.”
Identity Revolution Part 5: Integration. How Identity Ties Everything Together
The Complete Picture: Stablecoins + Agentic AI + Identity
1. Stablecoins: Money can move fast and cheaply (minutes, pennies)
2. Agentic AI: Intelligence makes fast money safe (real-time decisions, continuous learning)
3. Identity Infrastructure: Identity makes intelligent fast money trustworthy (verify continuously, protect appropriately)
None of them work alone. All of them work together.
Scenario: International Freelancer Payment (All Three Systems Working in Concert)
The Setup:
Freelancer in Mexico completes design work for company in New York
Company pays 5,000 USDC for the project
Traditional method: Wire transfer, 3-5 days, $175 in fees, opaque FX rates
New method: USDC via stablecoin rails
1. Stablecoin Handles:
Fast movement: Payment completes in 3 minutes (vs. 3-5 days)
Low cost: $12 total fees (vs. $175)
Transparent conversion: USDC → MXN at market rate +0.5% (vs. hidden 3% spread)
2. Agentic AI Handles:
Transaction monitoring: Is this legitimate payment or money laundering?
Pattern analysis: Company pays freelancers regularly (normal pattern)
Risk scoring: Low risk transaction (established relationship, expected amount)
Fraud detection: Neither party shows compromise indicators
Compliance: Automatic sanctions screening, AML checks
3. Identity Infrastructure Handles:
Verify sender: Is this really the company’s authorized payment agent?
Verify recipient: Is this really freelancer’s wallet address?
Continuous authentication: Both parties’ behavioral patterns match expected
Context verification: Payment amount matches invoice, timing matches project completion
Protection: If either wallet showed compromise signs, transaction would be held for review.
3:47 PM - Payment Initiated (New York)
Company’s treasury agent initiates 5,000 USDC payment to freelancer
Identity verifies: Agent has authority, acting within normal parameters
AI analyzes: Transaction fits expected pattern, no fraud indicators
Stablecoin moves: 5,000 USDC transfers on-chain
3:49 PM - Payment Received (Mexico)
Freelancers’ wallet receives 5,000 USDC
Identity verifies: This is the correct registered wallet, no compromise detected
AI monitors: The freelancer’s pattern is to convert USDC → MXN within 24 hours (typical for freelancers needing local currency)
Next day: Stablecoins are converted at freelancer’s preferred exchange, receives MXN in bank account
Total time: 2 minutes for payment, 1 day for conversion to local currency
Total cost: $12
Total trust: Verified at every step by identity + AI systems
Without Identity Infrastructure Layer: Transaction might be fast and cheap, but vulnerable to:
Compromised agent sending to wrong address
Stolen wallet credentials on freelancer’s side
Money laundering using freelancer payments as cover
Fraud from either party
Without AI Layer: Identity verification would catch obvious fraud but miss:
Sophisticated patterns (coordinated attack across multiple payments)
Timing-based attacks (sending during system maintenance windows)
Network-level threats (recipient wallet is part of criminal network)
Without Stablecoin Layer: Identity and AI can verify traditional wire transfer, but:
3-5 day settlement means fraud detected after money already cleared
No way to stop transaction mid-flight if compromise discovered
Opaque system makes pattern analysis harder
All three layers create a system that is fast AND cheap AND safe AND trustworthy. Remove any layer, and critical capabilities disappear.
(Note: If this article is truncated in your email, you can click on "View entire message" and you should be able to view the entire post in your email app.)
Identity Revolution Part 6: Why Traditional Infrastructure Can’t Do This (The Technical Reality)
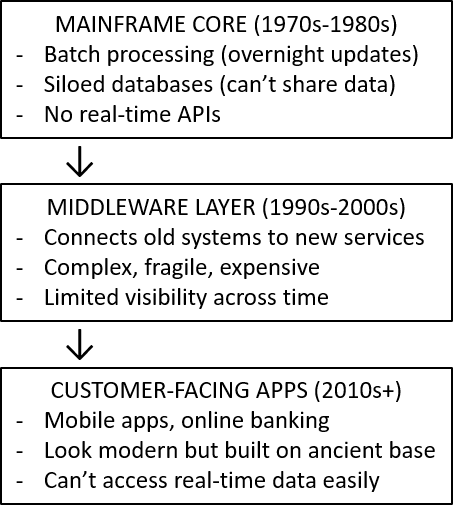
“Okay,” you might say, “traditional banks have identity verification and fraud detection. Why can’t they just upgrade their systems?” The answer is architectural. You can’t bolt these capabilities onto 1970s infrastructure any more than you can upgrade a horse-drawn carriage to a car by adding a motor.
The Legacy Banking Architecture (Why It’s Fundamentally Limited)
Traditional Bank Systems:
Why This Can’t Support Modern Identity:
Problem 1: Batch Processing
Bank systems update overnight (batch jobs run at midnight)
You transfer money at 2 PM, but fraud detection runs at midnight
By morning, fraudulent transfer has already settled
Modern identity needs: real-time verification during transaction, not 10 hours later
Problem 2: Data Silos
Account data in one system
Transaction history in another system
Customer service notes in a third system
Device fingerprinting in a fourth system
None of them talk to each other easily
Modern identity needs: “Give me everything about this customer in 100 milliseconds”
Legacy systems: “That query will take 15 minutes and might crash something important”
Problem 3: No Behavioral Analytics
Legacy systems track what happened (transaction log)
Don’t track how it happened (typing speed, mouse movements, navigation pattern)
Don’t have infrastructure to collect or analyze behavioral data
Modern identity needs: behavioral biometrics that legacy systems were never designed to capture
Problem 4: Human-Speed Decision Making
Legacy systems designed for humans reviewing transactions during business hours
Fraud analyst reviews flagged transactions Monday-Friday, 9-5
Modern identity needs: machine-speed decisions 24/7/365
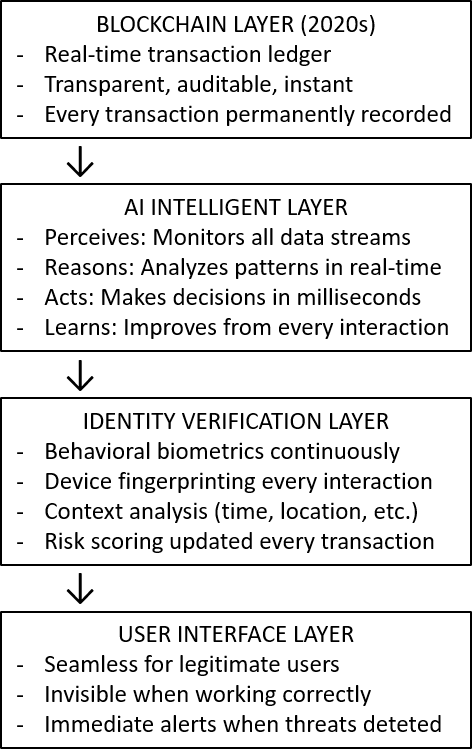
The Stablecoin + AI + Identity Infrastructure Layered Architecture (Why It Works Differently)
Why This Architecture Enables Modern Identity:
Advantage 1: Real-Time Everything
Blockchain: Transaction visible instantly
AI: Analyzing transaction while it’s pending (microseconds)
Identity: Verifying user behavioral patterns in real-time
Decision: Allow/block/challenge before transaction completes
Advantage 2: Unified Data
All systems access same data simultaneously
No silos, no waiting for batch updates
Identity system sees: blockchain transactions + user behavior + device data + external intelligence + historical patterns
All in one query, sub-second response time
Advantage 3: Built for Behavioral Analysis
System designed from the start to capture how users interact
Every keystroke, mouse movement, navigation path logged (with privacy protections)
Massive datasets enable AI to learn individual user patterns
Baseline established: “This is how the undergrad behaves normally”
Deviation detected: “This interaction doesn’t look like the undergrad”
Advantage 4: Machine-Speed Decisions
No human in the decision loop for routine transactions
AI + Identity system makes allow/block/challenge decision in milliseconds
Humans only involved for exceptions or appeals
Operates 24/7/365 without fatigue
The Migration Challenge (Why Banks Can’t Just “Upgrade”)
Unfortunately, many financial institutions for perceived monetary and time savings attempt to add AI and modern identity to their existing systems. The fundamental architecture isn’t capable of supporting them.
What Actually Happens:
When banks attempt to add behavioral biometrics:
Need to capture typing patterns - requires new instrumentation in web/mobile apps
Need to analyze in real-time - but core systems only update overnight
Need to store behavioral data - but databases weren’t designed for this data type
Need to query quickly - but systems take minutes to respond
Result: Compromised solution that’s slow, expensive, and not very effective
When banks attempt to add real-time fraud detection:
Need transaction data immediately - but transactions don’t hit fraud system until batch job runs
Need to block suspicious transactions - but transaction already sent to payment network
Need 24/7 monitoring - but systems designed for business hours, break under continuous load
Result: Fraud detected after the fact, too late to prevent loss
This is why stablecoins + AI + modern identity are being built as NEW infrastructure, not bolted onto old infrastructure. Today banks are understanding they can participate, but they’re building new systems in parallel, not trying to retrofit systems designed in the 1970s for a world that no longer exists.
Identity Revolution Part 7: The Future Is Now (What Happens Next)
We’re at an inflection point. The technology exists, the regulatory frameworks are emerging, the business case is proven. What happens in the next 2-5 years will determine the shape of global finance for the next 50 years.
2025-2026: Mainstream Institutional Adoption
Western Union is launching USDPT stablecoin in the First Half of 2026 (H1 2026 )
Visa is settling transactions in USDC on blockchain rails
PayPal is integrating PYUSD stablecoin across 400M users
Major Banks JPMorgan (JPM Coin) and others are building similar capabilities
Why Now:
Regulatory clarity (EU MiCA, US legislation pending)
Proven technology (billions moved daily without major incidents)
Competitive pressure (lose market share to competitors who move faster/cheaper)
Customer demand (businesses and individuals want faster, cheaper international payments)
The role of the modern identity infrastructure enables these institutions that won’t adopt without robust identity systems. Trust is their business. Modern identity makes stablecoins trustworthy enough for mainstream adoption.
2027-2028: The Agent Economy Emerges
The Vision: The buyer’s AI agent negotiates with supplier’s AI agent, agrees on terms, and executes payment autonomously. Goods ship, payment settles, all without human intervention until exception handling is needed.
Identity Requirements:
Agent identity certificates (proving agent is authorized)
Agent behavior monitoring (detecting compromised agents)
Multi-party authorization for high-value transactions
Audit trails for regulatory compliance
What This Enables:
24/7 commerce
Millisecond negotiations
Optimized outcomes (agents find best deals across thousands of options)
Reduced costs (eliminate human overhead for routine transactions)
The challenge is that agent identity verification is an unsolved problem today. By 2027, this must be standardized and robust. Otherwise, agent economy can’t happen at scale because there is too much fraud risk.
2029-2030: Identity as Competitive Advantage
In a world where everyone has fast, cheap stablecoin rails and AI agents, the institutions that invest in and successfully adopt identity systems will be the winners.
The Best Identity Systems Will:
Catch fraud others miss (lower losses)
False positive rate near zero (don’t block legitimate users)
Seamless user experience (invisible when working correctly)
Regulatory compliance built-in (reduce overhead)
Privacy-preserving (verify without exposing unnecessary data)
The Market Dynamics:
Users choose platforms with the best protection (after one fraud incident, they will switch)
Regulators favor institutions with demonstrated identity capabilities
Investors value lower fraud losses and regulatory risk
Best identity systems attract most users, get most data, improve fastest
The Long-Term Vision: Decentralized Identity
Currently each institution verifies you independently. Your identity data is siloed. You have little control. The emerging model is that you hold verified credentials in a digital wallet. You choose what to share, with whom, and when. Institutions verify credentials without a central database.
How It Works:
1. Credential Issuance:
Government issues: “Verified Adult” credential (proves age without revealing birthdate)
Bank issues: “Verified Customer” credential (proves account in good standing)
University issues: “Verified Graduate” credential (proves degree without transcript)
Employer issues: “Verified Employee” credential (proves employment without revealing salary)
2. Selective Disclosure:
Bank asks: “Are you over 18?”
You share: “Verified Adult” credential (proves yes without revealing exact age)
Bank verifies: Credential cryptographically valid, issued by trusted authority
Bank knows: You’re an adult
Bank doesn’t know: Your exact birthdate, full ID details, etc.
3. User Control:
You decide what to share
You can revoke access anytime
You see who accessed what, when
Data minimization: only share what’s necessary
Benefits:
Privacy: Share minimum necessary information
Convenience: Verify once (with government), use many times (with multiple banks)
Portability: Take your verified credentials anywhere
Control: You, not corporations, own your identity data
Challenges:
Standards still evolving (World Wide Web Consortium (W3C) Verifiable Credentials, Data Item Descriptions (DIDs))
Recovery mechanisms (if you lose wallet, how do you prove identity?)
Regulatory acceptance (will institutions trust external credentials?)
User adoption (requires new mental model and behaviors)
Time is of the essence. Early pilots are now being architected with mainstream adoption probably 2028-2030. Universal system probably 2035+.
The Personal Stakes
Right now:
Your passwords are probably compromised (most data breaches haven’t been disclosed yet)
Your biometric data exists in databases you don’t control
Your behavioral patterns are being tracked (often without explicit consent)
Your identity is being verified (or failing to be verified) constantly
In 5 years:
AI agents may manage your finances (with identity certificates you approve)
Decentralized identity may give you control over your data
Continuous identity verification may protect you from fraud you never even see
Your digital identity may be more valuable than your physical assets
The questions everyone should ask:
Who has my identity data, and what are they doing with it?
How can I protect myself in a world of deepfakes and AI-powered fraud?
What rights do I have over my own identity information?
How do I verify that AI agents are trustworthy before granting them authority?
This isn’t distant future. This is 2025-2030.
Understanding identity, not just as a technical system but as social infrastructure, positions you to navigate this transformation successfully, whether as builder, user, regulator, or informed citizen.
Identity Revolution Part 9: The Integration Complete (Bringing It All Together)
1. Stablecoins: Moving 50,000 USDC is faster and cheaper than traditional rails: minutes vs. days, and dollars vs. hundreds in fees. The technology enables speed.
2. Agentic AI: The system monitoring this transaction is an agentic AI that perceives dozens of signals simultaneously, reasons about whether patterns match normal behavior, acts by allowing or blocking based on risk, and learns from every interaction to improve. The intelligence enables safety.
3. Identity Infrastructure: The question “Is this really you?” is being answered with “yes, this interaction matches his behavioral patterns across 100+ dimensions measured in real-time with 95% confidence.” The continuous identity verification enables trust.
Stablecoins can move money at internet speed. AI can make intelligent decisions in milliseconds. But without identity systems sophisticated enough to verify trust continuously, none of it matters. Speed without trust is just fast fraud.
The old world: Verify identity once, hope nothing changes, deal with fraud after the fact.
The new world: Verify identity continuously, detect threats before they succeed, protect users from risks they never even see.
This isn’t just technical innovation. It’s a fundamental reimagining of how trust works in digital systems and it’s happening right now, whether we are ready or not.
All three together create something that is impossible with only any two:
Stablecoins alone: Fast and cheap, but vulnerable to fraud
Stablecoins + AI: Fast, cheap, and smart, but can’t verify humans effectively
Stablecoins + Identity: Fast, cheap, and verifiable, but lacks intelligence to catch sophisticated attacks
AI + Identity without stablecoins: Can verify but stuck with slow, expensive legacy rails
Only the integration of all three enables: Fast + Cheap + Safe + Trustworthy + Scalable
That’s why this is transformation, not just improvement. The question, “Is this really you?” is the question that determines whether this financial revolution succeeds or fails.
CONCLUSION
When authoring this series, we didn’t want to ignore legitimate concerns about AI’s central role in our evolving international financial systems. We understand the concerns, and it is right to be cautious about AI’s power, control, and potential unintended consequences. But history shows technology fears often overestimate risk.
There are historical parallels:
1800s: Trains: Traveling faster than horses will cause insanity.
1900s: Electricity: Dangerous force that will kill everyone.
1970s: Computers: Will eliminate all jobs and control society
2000s: Internet: Will destroy privacy and enable totalitarian control
Initial fears focus on worst-case scenarios. Reality is more nuanced. Technology brings both benefits and risks. These can be managed through thoughtful design, regulatory frameworks, social norms and expectations, and continuous improvement based upon experience. AI in finance will follow similar patterns by having early deployment with oversight that includes learning from experience/mistakes with gradual refinement of safeguards to eventual normalized adoption with clear rules such as:
Technical - bounded authority, explainable requirements, audit trails, performance monitoring
Human - oversight transparency, exception handling, policy control, override authority, shutdown authority
Regulatory - government oversight, liability rules, testing requirements, ongoing compliance
These are published and vetted core requirements for AI deployment in regulated industries.
It’s important to distinguish between AI taking over decision-making versus AI taking over control. What we are describing isn’t AI replacing human judgment; it’s AI operating within strict boundaries set by humans. The real risks don’t come from a potential AI takeover where AI becomes sentient and seizes control. The real risks come from humans abdicating responsibility by deploying AI systems without proper oversight mechanisms, clear accountability structures, explainability requirements, human review of edge cases, kill switches, and circuit breakers.
Every described AI supported financial system includes human oversight, bounded authority, explainability, and accountability. We’re not saying let AI decide everything, we’re saying let AI handle routine tasks while humans focus on strategic decisions and exception handling. We are describing evolving financial systems as augmentative, not replacements; supplementing, not supplanting.
Similar to stablecoin and evolving international finance systems, AI is already making critical systems safer like credit card fraud detection, air traffic control, medical diagnosis, fraud detection and power grid management.
The alternative to AI Is riskier. What “don’t use AI in modern finance” actually means:
Fraud detection: Humans review transactions overnight → fraud discovered too late, money already stolen
Identity verification: Password-only authentication → deepfakes and credential theft succeed easily
Reserve management: Humans make daily decisions → miss optimization opportunities, earn $100M less annually
Crisis response: Wait for human committee meeting → 30-60 minute delay allows panic to spread
The result:
More fraud (customers lose money)
Slower systems (worse user experience)
Higher costs (passed to consumers)
More human error (fatigue, distraction, bias)
Unfortunately, this is not theoretical. Before AI fraud detection, credit card fraud rates were 3-4x higher than today. AI didn’t take over. It protected people better than human-only systems could. Once again, the question isn’t “AI vs. no AI”, it’s “AI with proper safeguards vs. inadequate human-only systems that can’t keep up with digital-speed threats.”
In response to today’s realities, concerns shift the conversation from “should we use AI?” (we already are) to “how do we use AI responsibly?” Through experience, leveraging multiple domain expertise, responsible AI deployment is requiring:
Transparency: Users know when AI is making decisions
Explainability: AI can explain its reasoning in human terms
Accountability: Humans remain liable for AI actions
Fairness: AI doesn’t discriminate based on protected characteristics
Privacy: AI protects user data while performing verification
Oversight: Humans monitor AI performance continuously
Recourse: Humans can appeal AI decisions
Safety: Multiple layers of safeguards prevent catastrophic failures
In summary, the concern about AI taking over is understandable. However, the real risk isn’t AI gaining independence, but humans deploying AI without proper safeguards.
If our AI research sparked something valuable for you, leaving a tip below helps us keep processing the future. We appreciate every acknowledgment. Sincerely.


This article should be taught in schools, so the present and coming generations know exactly what their world is going to look like.
It will be curious to see if banks ever change the number of days it takes to withdraw the money that moves at speed. Even today, banks with sophisticated ways seem to cling to outdated "paper" processes that wait for three days to clear the funds. Is this another example of the technology being ahead of the human mentality to cling to the comfortable past? The proverbial batch job that has to run, even though the data is already here. The tellers kept the "daily report" to give them a sense of pseudo-comfort that all is right with the world - even if they never read it.
I particularly liked the section on the agent identity problem. Who shall guard the guardians?
"Your digital identity may be more valuable than your physical assets". - Don, I think we're already there?
Beautiful article, Don - thank you.